Passwords have always been the standard when it comes to securing online accounts. For decades, information security experts have promoted the use of complex passwords that contain random letters, numbers, and special characters, such as “h0r5E$Ho3s+ICk”. However, through brute force attacks and other nefarious tactics, cybercriminals can now easily guess even these types of passwords, jeopardizing data security more than ever.
Passwords vs. passphrases: Which one should you use?
USWired’s ultimate guide to managed IT services

Technology is rapidly evolving, and businesses must keep up with it to stay relevant and profitable. Back in the day, most companies managed their IT infrastructure by hiring in-house staff to get better control over their operations.But as their operations grow and become more reliant on technology, in-house IT teams have difficulty managing everything by themselves.
How to foster a security culture in your business
Best security practices for your Office 365 subscription

Many businesses today rely on Office 365 to improve productivity and efficiency in the office. Its vast array of programs such as Word, Excel, PowerPoint, Teams, and OneDrive helps users get work done faster.
While the platform is generally safe to use, thanks to its Exchange Online Protection feature, cybercriminals are still continuously finding ways to steal data from unsuspecting users.
Signs your network infrastructure needs an upgrade
What are the most common phishing tactics online?
Best practices for an effective backup strategy

Your data is the lifeblood of your business, so it's important to ensure it's not suddenly erased or fallen into the wrong hands. Power failures, floods, earthquakes, and even cyberattacks can immediately impact operations, and they can also have a long-term effect on your profits, reputation, and employee morale.
How to prevent security breaches in Office 365

Office 365 is a tried-and-tested subscription service that enables businesses to save countless hours doing repetitive and manual work. With its programs such as Word, Excel, PowerPoint, OneDrive, and Teams, among many others, the platform allows users to access documents on mobile devices, organize teamwork, and analyze work activities.
A handy network security checklist for small businesses

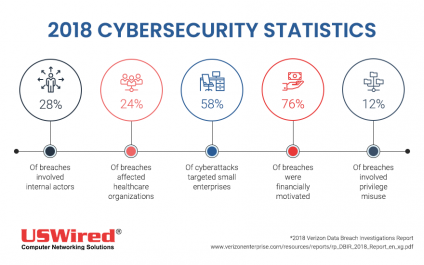
Large enterprises aren't the only ones vulnerable to cyberattacks. Contrary to popular belief, small- and medium-sized businesses (SMBs) also fall victim to cybercrime. Verizon’s 2018 Data Breach Investigations Report found that 58% of cyberattacks target small organizations, and these are fueled by business owners’ negligence toward protecting their IT infrastructure.
Disaster recovery statistics business owners need to know
It’s important for businesses to always be prepared for unexpected events. Natural and man-made disasters such as earthquakes, storms, and cyberattacks can occur anytime, and a detailed course of action can mitigate the gravity of their effects.
Your disaster recovery strategy should always focus on your data.