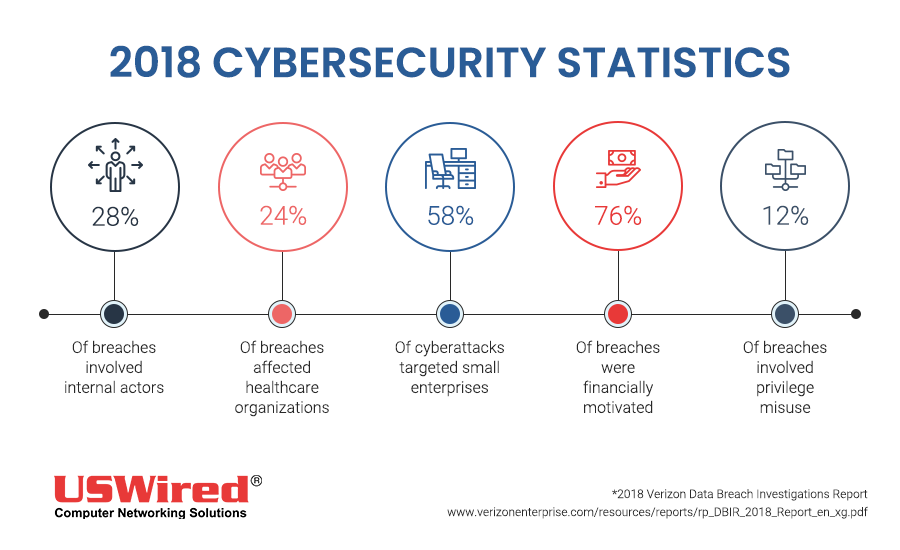
Large enterprises aren't the only ones vulnerable to cyberattacks. Contrary to popular belief, small- and medium-sized businesses (SMBs) also fall victim to cybercrime. Verizon’s 2018 Data Breach Investigations Report found that 58% of cyberattacks target small organizations, and these are fueled by business owners’ negligence toward protecting their IT infrastructure.
Given this, it’s becoming highly crucial for SMBs to build a strong cybersecurity foundation to protect their data and employees. In a world where cyberthreats are becoming more complicated by the day, it helps to have a handy guide that organizations can follow when it comes to securing their systems.
Here’s a five-step security checklist you can follow:
#1. Invest in effective endpoint security
Endpoint security refers to the protection of your IT infrastructure when accessed via an internet-capable device such as desktops, laptops, tablets, smartphones, and other mobile devices. If these gadgets connect to your network and aren’t properly configured, they become a potential entry point for cyberthreats.
Let’s say one of your employees is working on a confidential project via a cafe’s public Wi-Fi connection. Files for the project are archived in your cloud-based network, so accessing these through unsecure channels such as public Wi-Fi allows hackers to intercept the relay of data and either steal your files or upload malicious files of their own into your systems. As many people are still negligent about installing critical patches and updates, these devices, or “endpoints,” can become a cause for disaster.
To combat this, invest in effective endpoint security. These typically include firewalls, antivirus and anti-malware software, internet security tools, and mobile device management (MDM) tools, among others. This ensures that the devices connected to your network are always protected from any issues.
#2. Establish an incident response plan
What are the biggest threats that your company is facing? Are employees falling for phishing scams? Are ransomware attacks becoming rampant? Record all of the most common incidents that are happening in your office, and from there, develop incident response and disaster recovery plans.
Related article: The biggest challenges to cybersecurity in 2019
For instance, if hardware failure is a persistent problem in the workplace, you can replace your equipment with newer ones that are less prone to crashing. As for phishing attacks, identify the malicious email and see who was targeted. Hold a company-wide review to assess and control the damage done. Finally, train staff on what mistakes were made so future incidents can be prevented.
You can conduct “live fire” exercises that involve sending a fake phishing email to all employees, and record how many people fall for it. From there, you can tailor your incident response plan better.
When it comes to clients, maintaining their trust is non-negotiable. If cybercriminals or other parties compromise their data, they will need transparent communication and steady reassurance that you are working hard to resolve the issue and their data is safe.
#3. Evaluate your IT security resources
Whether you’re an SMB or a large corporation, IT security will always be an important aspect of your operations. With the alarming rise of targeted threats, it’s crucial for your business to designate your IT resources such as servers, phone systems, and software to the right people.
You can partner with managed IT service providers (MSPs) such as USWired that can make good use of your security resources and ensure your protection against the latest threats. MSPs are a team of well-rounded IT experts that can monitor your IT infrastructure 24/7/365 and prevent data breaches from happening. The best part? They charge a flat monthly fee that costs less than paying an in-house staff a full-time salary.
Related article: New cybersecurity threats we all should watch out for in 2019
#4. Create a strong password policy and implement multifactor authentication
Whether we like them or not, passwords are the current standard when it comes to securing data online. Instead of using passwords that are composed of numbers and characters, use sentences or a group of words such as “idrinkcoffeeeveryday” or “runstoryborderlands1256”.
Require password changes only when data breaches occur so as to avoid password overload among your employees. Finally, make use of multifactor authentication (MFA). This technology makes use of at least two means of verifying a user’s identity.
For example, after your users enter their password, you can also require them to input a code delivered to their smartphone. This way, stealing the password won’t be enough for cybercriminals to get to your data, as they would also need the secondary verification method.
#5. Constantly update your policies
Cybersecurity will always be an unending endeavor, and as cliché as it may seem, remember that prevention will always be better than cure. Regularly examine your company’s IT policies and procedures, and be aware of the latest threats that can endanger the security of your data. When cybersecurity is done right, it will help ensure that your business isn’t held back by cyberthreats.
Need peace of mind for your business? USWired offers a Cybersecurity service that provides advanced threat protection, and reliable mobility and endpoint solutions. We’re ready to be your partner for success no matter the circumstance. Call us today to know more.