In the past, business phone systems were synonymous with bulky hardware, complicated wiring, and limited features. These traditional systems anchored companies to their desks and imposed hefty maintenance costs. However, the rise of new technologies has revolutionized business communication.
Navigating the new age of business phone systems
Fully managed vs co-managed IT: What’s the difference?

Choosing the right IT management approach is critical for business efficiency and security. Two leading models, co-managed and managed IT services, offer distinct advantages. In this blog post, we will define the key differences between co-managed and fully managed IT to help you make an informed decision that aligns with your specific business needs.
Managed IT: Freeing your team to focus on what matters most

Cloud computing and other essential IT infrastructure solutions are critical for business success. However, possessing the in-house expertise to fully manage and support such technologies can be a significant challenge. The ever-expanding IT skill set landscape makes hiring a dedicated professional for every situation unrealistic and financially burdensome.
Mastering your presentation skills: A guide to using PowerPoint Presenter Coach
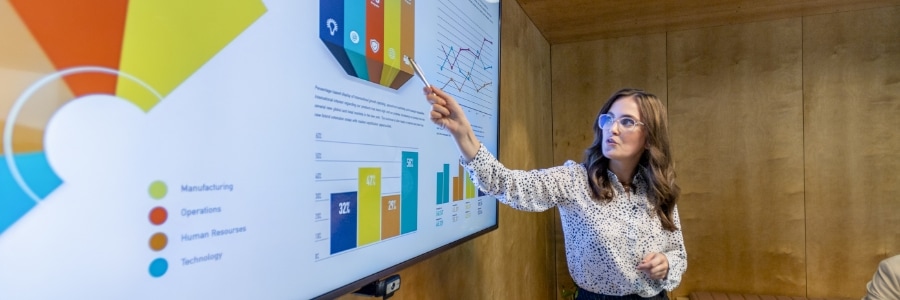
Giving a PowerPoint presentation doesn't have to be a daunting task with the right tools. PowerPoint Presenter Coach is one such tool that's designed to help you hone your presentation skills and boost your confidence. Whether you're preparing for a business meeting or a public speaking event, this guide will show you how to make the most of PowerPoint Presenter Coach to deliver a polished, professional presentation every time.
The VoIP revolution: Future-proofing business communications
Common IT investment mistakes to avoid
Key practices to strengthen your email security posture

Email remains a cornerstone of modern business communication, valued for its speed, ease of use, and convenience. However, it also presents a potential vulnerability in the face of cyberattacks. By implementing the following practical measures, you can significantly enhance your email security posture and protect your valuable business information.
Unlocking the full potential of remote work with VoIP

As businesses adapt to the evolving landscape of remote work, the need for robust and efficient communication tools becomes increasingly critical. Voice over Internet Protocol (VoIP) offers a revolutionary approach to remote communication, providing unmatched accessibility and a host of features designed to keep teams connected and productive.






