What do you call someone who hunts for security gaps in computer hardware and software? A hacker, right? What about someone who executes a vulnerability test and presents their findings to software vendors to help them improve the quality of their products? There is more than one type of hacker, and understanding the difference is important.
Support Center
Cybersecurity mistakes to avoid in 2020

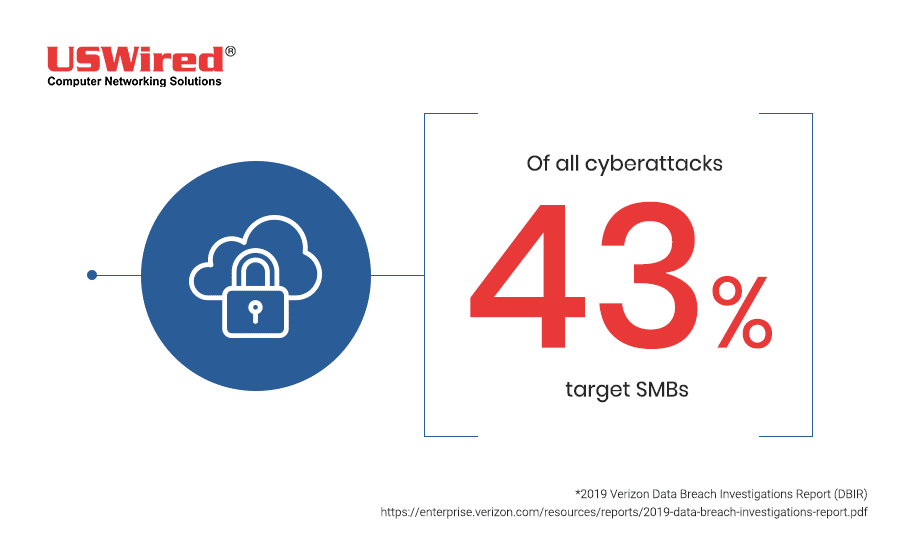
Cyberthreats are becoming more dangerous every year. Cybercriminals are not only becoming more successful at stealing the data of large companies but also those of small- to medium-sized businesses (SMBs) because of their security negligence.
But while those threats are imminent, we at USWired believe that it's never too late to start protecting your businesses from threats such as malware, phishing, and denial-of-service (DoS) attacks.
Do these before buying cybersecurity software
Office 365 hacking: What you need to know

Some hackers have become so skilled that they don’t even need you to give up your credentials to hack into your account. One recent cyberthreat is targeted towards users of Microsoft Office 365. You don’t want to be the next victim, so read up.
A phishing scam that harvests users’ credentials
The latest cyberattack on Microsoft Office 365 involves harvesting users’ credentials.
Protect your business from these top cyberthreats in 2020

Cybercriminals successfully launched ransomware, phishing, anattacks on businesses in 2019. And it will be more difficult to stop them as they constantly improve their methods to steal more confidential business data.
According to Gartner’s forecast, worldwide spending on cybersecurity is expected to reach $170.4 billion in 2022. This is due to security leaders striving to bolster their organizations' security with technology that drives growth and keeps data secure.
What are the different types of malware your business has to look out for?

Cybercrime is a lucrative business, and this is why cybercriminals continue to devise new techniques to trick individuals and businesses into handing other money or confidential information, which they can then exploit or sell on the dark web.
One of the most common techniques that cybercriminals use is malware.
Mitigating cybersecurity insider threats

Did you know that in some industries the biggest cybersecurity threats come from inside a breached organization? Sometimes it's motivated by financial gain and sometimes it's plain-old ignorance. So how can you protect your organization from insider threats?
#1 Educate
You must teach your team to recognize personally identifiable information (PII) and understand the financial implications of a breach.
Security audits are more crucial than they seem
How to prevent business email compromise
The top cybersecurity myths hackers want businesses to believe
The world of cybersecurity can be pretty confusing, and the endless news about hackers, malware, and data breaches aren’t helping businesses understand it any better. This leads many users to believe in many exaggerations and fallacies. Some think that believing in myths is harmless, but if it actually costs you your precious data and hard-earned revenue, it can be significantly damaging.





