The world of cybersecurity can be pretty confusing, and the endless news about hackers, malware, and data breaches aren’t helping businesses understand it any better. This leads many users to believe in many exaggerations and fallacies. Some think that believing in myths is harmless, but if it actually costs you your precious data and hard-earned revenue, it can be significantly damaging.
Let’s take a look at the most popular cybersecurity myths that hackers want you to believe:
#1. Your business can’t be a victim
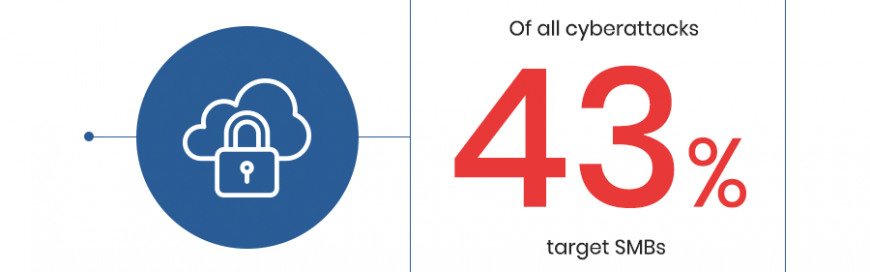
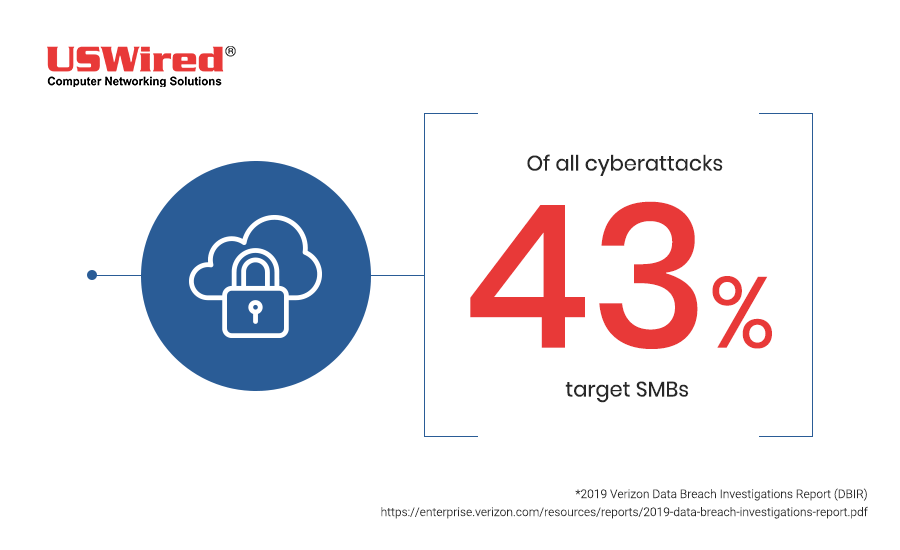
Some business owners tend to think that their companies aren’t likely to become victims of cyberattacks like malware, phishing, and distributed denial-of-service (DDoS) attacks. This is a dangerous mindset, however. Cybercriminals are constantly devising new ways to assault businesses of all sizes, and the number of cyberattacks has been increasing as a result.
According to the 2019 Verizon Data Breach Investigations Report (DBIR), 43% of cyberattacks target small businesses. Cybercriminals are aware that small firms don’t have proper security solutions installed in their networks, and they are taking advantage of this negligence to attack and steal small businesses’ data.
#2. Your passwords are strong enough
It’s always been advised to create a strong password to prevent hackers from accessing your online accounts and stealing confidential information. However, cybercriminals can now crack passwords more easily through brute force attacks. These use a trial-and-error method to guess a user’s password until it is cracked. By learning how users create passwords and then using automated bots to come up with tens of thousands of password iterations, hackers can try a large number of possible keywords to try and access an account.
Don't rely solely on passwords. Make your business more secure through multifactor authentication (MFA). This uses more than one method to verify a user’s identity. These methods include fingerprint, face or iris scan, or a one-time smartphone code. Even if a hacker acquires a user’s login credentials, their login attempt would be futile without fulfilling the other verification steps.
#3. You can’t get infected when you don’t visit unsafe websites
If you’re doing your part to stay safe online by not visiting sketchy websites that might be loaded with malware, then good for you. The fight against cyberattacks doesn’t stop there, though. Hackers are aware that many people think it's entirely safe to browse the websites they trust. They take advantage of this thinking, and hijack and inject rogue content into trusted websites.
Attackers can also compromise your business’ security through other means. Phishing, for one, involves an innocuous-looking email that steals your login credentials. Mobile devices can also be an entry point for hackers. If a user connects to a public Wi-Fi network and uses it for work purposes, cybercriminals can easily infiltrate the device and steal sensitive information. Unsupported operating systems like Windows XP can also be an entry point for malware and other attacks.
Installing an effective antivirus software can significantly help in preventing malware from infecting your system. Training your employees to spot phishing emails, refrain from using public Wi-Fi, and keep their systems updated will bolster cybersecurity as well.
#4. Investing in security solutions is expensive
Businesses that have a very tight budget might think that investing in security solutions such as antivirus software, firewalls, intrusion prevention systems (IPS), and employee training is a useless expense.
The problem with this line of thinking is that the costs of cyberattacks are not considered. According to insurance carrier Hiscox, cyberattacks cost small companies $200,000 on average. To make things worse, 60% of them go out of business within six months of being victimized.
Spending money on security solutions might be costly at first, but remember that it is far less expensive than the costs of recovering from a data breach.
Download our free eBook!
Read our free eBook: 3 Types of Cyber Security Solutions Your Business Must Have and find out how to protect your business and optimize your solutions without breaking the bank
#5. Cyberthreats are mostly external
Have you ever thought that your own staff could also be a threat to your data’s security? According to Verizon, 34% of all breaches in 2018 were caused by insiders.
Why would the people in your company become the cause of security breaches? It might be due to carelessness or lack of training. Some might even unwittingly expose your data to hackers through their personal smartphones. Disgruntled current and past employees can be a factor, as they might have a desire for revenge or professional gain.
You can use access management solutions such as Azure Information Protection (AIP) and Microsoft Intune to mitigate internal attacks. The former classifies data based on sensitivity and makes it possible to add visibility and control permissions, so your sensitive company files will only be visible to executives and other authorized employees. The latter regulates mobile devices being used to access corporate apps and data.
Cybercriminals are becoming more persistent than ever at disrupting your security infrastructure. Here at USWired, we offer comprehensive network security plans that monitor, analyze, and stop attacks 24/7/365. The best part? We charge a flat monthly fee that’s cheaper than a full-time IT employee’s salary. Contact us today to get started.