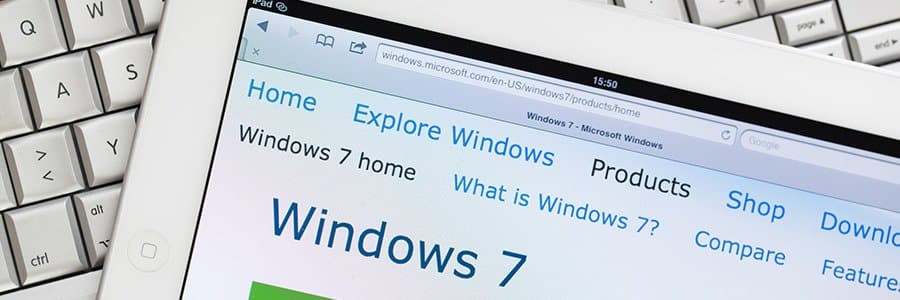
In less than two months, Microsoft will be pulling the plug on the Windows 7 operating system (OS). This means that all technical support, software updates, and security patches will no longer be available for the OS. All systems running Windows 7 will eventually become vulnerable to cyberthreats such as malware, phishing, and denial-of-service (DoS) attacks, among others.
877-879-4733
Support Center
Support Center
Blog
Your future is with VoIP telephony systems

When it comes to IT, easy set-up, flexibility, and savings are music to the ears of any owner of a small- or mid-sized business (SMB). These are all features that contribute to the success of Voice over Internet Protocol, or VoIP. The technology was built on a strong foundation that has allowed it to move with the times.
Office 365 productivity add-ons you must use
Taking business continuity to the cloud
Security audits are more crucial than they seem
How to prevent business email compromise
TDoS: An attack on VoIP systems
Office 365 feature highlight: Predictive forecasting
The top cybersecurity myths hackers want businesses to believe
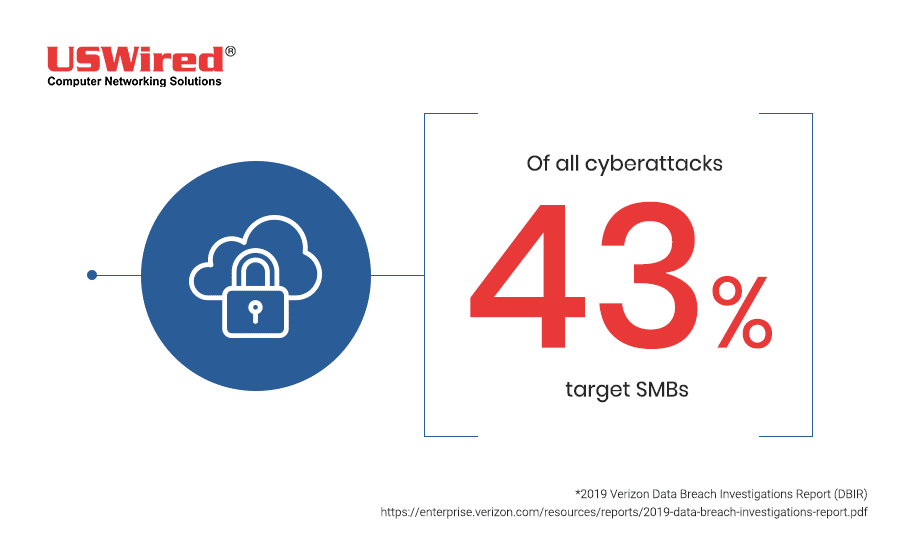
The world of cybersecurity can be pretty confusing, and the endless news about hackers, malware, and data breaches aren’t helping businesses understand it any better. This leads many users to believe in many exaggerations and fallacies. Some think that believing in myths is harmless, but if it actually costs you your precious data and hard-earned revenue, it can be significantly damaging.