Business continuity is often overlooked until it’s too late. But with the cloud on their side, IT departments and business owners can more easily adopt this strategy to help avert the next outage. Here’s how the cloud benefits implementations of business continuity.
Taking business continuity to the cloud
Security audits are more crucial than they seem
How to prevent business email compromise
TDoS: An attack on VoIP systems
Office 365 feature highlight: Predictive forecasting
The top cybersecurity myths hackers want businesses to believe
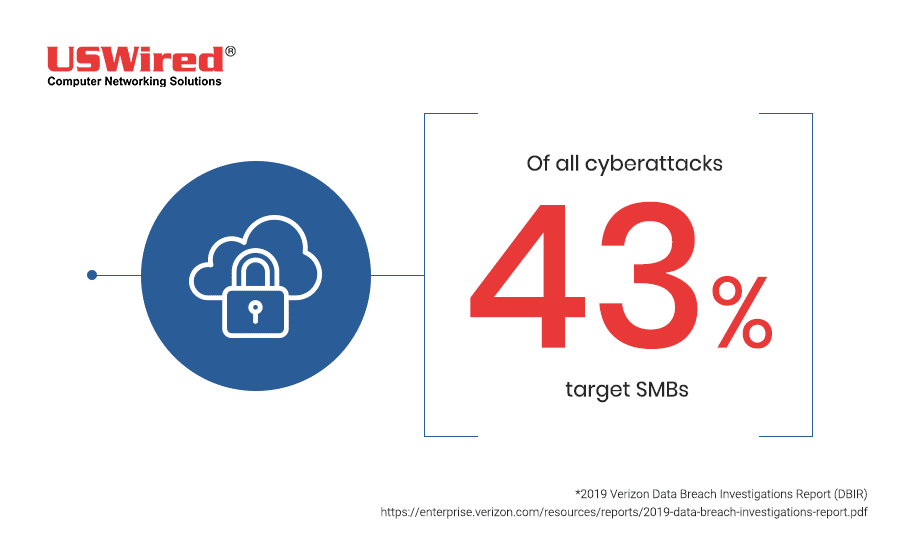
The world of cybersecurity can be pretty confusing, and the endless news about hackers, malware, and data breaches aren’t helping businesses understand it any better. This leads many users to believe in many exaggerations and fallacies. Some think that believing in myths is harmless, but if it actually costs you your precious data and hard-earned revenue, it can be significantly damaging.
BI is not just for the big boys
How to strengthen your BYOD security
What is VoIP theft of service?
Passwords vs. passphrases: Which one should you use?

Passwords have always been the standard when it comes to securing online accounts. For decades, information security experts have promoted the use of complex passwords that contain random letters, numbers, and special characters, such as “h0r5E$Ho3s+ICk”. However, through brute force attacks and other nefarious tactics, cybercriminals can now easily guess even these types of passwords, jeopardizing data security more than ever.