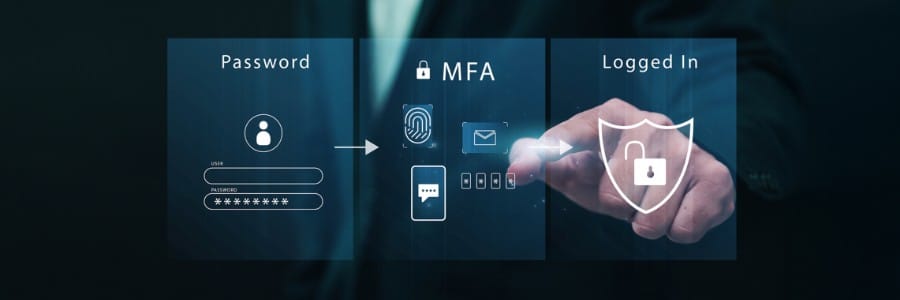
Multifactor authentication (MFA) works by requiring users to provide more than one form of identification when logging into a system or account. This extra layer of security is meant to prevent unauthorized access and protect sensitive information. However, while MFA may seem like a foolproof solution, it actually has its own set of vulnerabilities that can be exploited by cybercriminals.
Support Center
Blog
Choosing between cloud and on-site VoIP hosting: A guide for businesses

With Voice over Internet Protocol (VoIP) becoming increasingly more common for businesses, business leaders must choose between cloud and on-premises hosting, both of which offer distinct advantages and challenges. This article outlines the essential factors to consider when selecting the most optimal hosting option for your company.
Why Microsoft Whiteboard is becoming a go-to tool for team collaboration
Defending against data loss: 6 Strategies businesses should implement
How to maximize efficiency with Microsoft 365: The essential guide
2026 Cybersecurity trends and predictions

Cybersecurity experts Rob Wright (Dark Reading), David Jones (Cybersecurity Dive), and Alissa Irei (TechTarget Search Security) recently came together to discuss the future of online security. Let’s take a look at their insights on major trends and new risks to help businesses better navigate the challenges on the horizon.
5 Ways VoIP phone systems are getting smarter (and what it means for you)
How IT consulting can set SMBs up for success in 2026
Tips for creating more secure business passwords
How to solve the most common VoIP call glitches

Clear, reliable communication is critical for any business, and VoIP systems make that easier and more affordable than ever. However, if your calls are plagued by lag, echo, or unexplained silence, the benefits can quickly turn into headaches. Understanding the root causes of these common issues is the first step toward ensuring smooth, reliable calls.